Anycasting: Difference between revisions
imported>Howard C. Berkowitz No edit summary |
imported>Howard C. Berkowitz (Added references and examples, changing status to 1) |
||
| Line 3: | Line 3: | ||
| id = RFC4291 | | id = RFC4291 | ||
| title = IP Version 6 Addressing Architecture. | | title = IP Version 6 Addressing Architecture. | ||
| | | first1 =R.|last1=Hinden |first2= S. | last2=Deering. | ||
| date = February 2006 | | date = February 2006 | ||
| url = http://www.ietf.org/rfc/rfc4291.txt}}</ref> it can be quite useful with IPv4. The technique, while somewhat counterintuitive, is useful for load distribution, fault tolerance, or both. | | url = http://www.ietf.org/rfc/rfc4291.txt}}</ref> it can be quite useful with IPv4. The technique, while somewhat counterintuitive, is useful for load distribution, fault tolerance, or both. IPv4 has no infrastructure explicitly for anycast while IPv6 does, but the technique can be applied in both areas, with different address structures. Miller discusses "shared anycast",<ref name=>{{citation | ||
| url = http://www.net.cmu.edu/pres/anycast/Deploying%20IP%20Anycast.ppt | |||
| title = Deploying IP Anycast | |||
| first1 = Kevin | last1 = Miller | |||
| date = NANOG 29 – October 2003}}</ref>, which is different than the IPv6 specific work in RFC4291, which superceded the RFC3513 mentioned in the Miller paper. | |||
Traditionally, an IP address, inside a given routing/addressing domain, needed to be unique. In this discussion, assume 3.1.1.1 is the address of a server. That is indeed true in a "flat" address space of a single IP subnet (i.e., network prefix). When the environment is split by routers into logical subnets, remember that a router commonly receives different paths to what it assumes is the same address, picks the "best", and puts the associated prefix and outgoing address and puts that in its routing table. It was realized, however, that the router, unless very deliberate steps are taken, really does not know if two potential paths to an address are merely different ways to get to the same instance of an address, or if they represent unique paths to different instances of the address. | Traditionally, an IP address, inside a given routing/addressing domain, needed to be unique. In this discussion, assume 3.1.1.1 is the address of a server. That is indeed true in a "flat" address space of a single IP subnet (i.e., network prefix). When the environment is split by routers into logical subnets, remember that a router commonly receives different paths to what it assumes is the same address, picks the "best", and puts the associated prefix and outgoing address and puts that in its routing table. It was realized, however, that the router, unless very deliberate steps are taken, really does not know if two potential paths to an address are merely different ways to get to the same instance of an address, or if they represent unique paths to different instances of the address. | ||
| Line 27: | Line 31: | ||
Of course, if client 2 reconnected to Router 3, it would have the lowest cost path to server C as long as Server C stayed up. If Server C fails, router 3 would change its route to 3.1.1.1 to the path to Server B. | Of course, if client 2 reconnected to Router 3, it would have the lowest cost path to server C as long as Server C stayed up. If Server C fails, router 3 would change its route to 3.1.1.1 to the path to Server B. | ||
==Operational examples== | ==Operational examples== | ||
Anycast works well for any application that is read-only and where the relevant servers have a common database. One common application is the root servers for the [[Domain Name Service]].<ref name=RootServer>{{citation | |||
| title = Root Server Anycast Status | |||
| url = http://gac.icann.org/web/meetings/mtg22/RootServerAnycastStatus.ppt}}</ref> Another application is in [[Internet Protocol]] infrastructure security. Large operators may have multiple [[sinkhole]]s <ref>{{citation | | |||
|url = http://www.arbornetworks.com/downloads/Sinkhole_Tutorial_June03.pdf | |||
| title = Sinkholes: A Swiss Army Knife ISP Security Tool Version 1.8 | |||
| first1 = Barry Raveendran | last1 = Greene | first2 = Danny | last2 = Macpherson}}</ref> for analyzing hostile traffic; the sinkhole nearest the ingress router does the analysis of a single-stream denial of service (DoS) attack, while anycast-addressed sinkholes respond well under distributed denial of service (DDoS) attack. | |||
Router interface addresses that are unicast need more care in configuration, but are still feasible.<ref name=Kristoff>{{citation | |||
| author = John Kristoff | |||
| title = Anycast Addressing on the Internet | |||
| date = January 2, 2004 | |||
| contribution = Anycast Routing | |||
| url =https://www.kuro5hin.org/story/2003/12/31/173152/86 }}</ref> When using anycast with routers, it is best to use a routing protocol, such as the [[Border Gateway Protocol]] or [[Open Shortest Path First]], that has an explicit router identifier that can disambiguate different announcements of the same address. | |||
==References== | ==References== | ||
{{reflist}} | {{reflist|2}} | ||
Revision as of 09:40, 15 September 2008
Please create the "Talk page". Just click this Talk page link and save the page.
While the term anycast came into prominence with IPv6 work,[1] it can be quite useful with IPv4. The technique, while somewhat counterintuitive, is useful for load distribution, fault tolerance, or both. IPv4 has no infrastructure explicitly for anycast while IPv6 does, but the technique can be applied in both areas, with different address structures. Miller discusses "shared anycast",[2], which is different than the IPv6 specific work in RFC4291, which superceded the RFC3513 mentioned in the Miller paper.
Traditionally, an IP address, inside a given routing/addressing domain, needed to be unique. In this discussion, assume 3.1.1.1 is the address of a server. That is indeed true in a "flat" address space of a single IP subnet (i.e., network prefix). When the environment is split by routers into logical subnets, remember that a router commonly receives different paths to what it assumes is the same address, picks the "best", and puts the associated prefix and outgoing address and puts that in its routing table. It was realized, however, that the router, unless very deliberate steps are taken, really does not know if two potential paths to an address are merely different ways to get to the same instance of an address, or if they represent unique paths to different instances of the address.
As long as the behavior of multiple instances of the address are identical, it makes no difference, to the requesting client, if server A, B, or C actually executes the request.
The IPv6 architecture describes it as:
Anycast: An identifier for a set of interfaces (typically belonging to different nodes). A packet sent to an anycast address is delivered to one of the interfaces identified by that address (the "nearest" one, according to the routing protocols' measure of distance).[1]
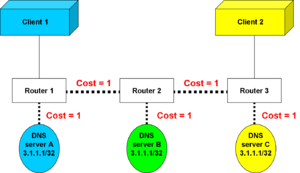
Load balancing case
In the illustration to the left, there are three instances of a server, which carries out a read-only function; it makes no difference to the client which server actually satisfies its request.
The simplistic routing mechanism here adds up the costs of routes to a destination. From router 1, server A is closest. From router 3, server C has the least cost.
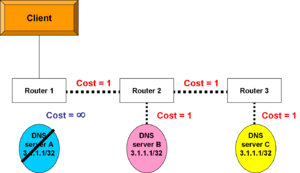
Fault tolerance case
Now, simplify the scenario to have but one host. As long as server A is up, router 1 will see a cost of 1 to reach server A. The routing process was aware of other routes to 3.1.1.1, but there was a cost of 2 to server B and a cost of 3 to server C. Router 1 only put the lowest-cost route into its routing table.
But what if server A fails? The router knows other paths to the same address, so it will install the path that goes through router 2. The client will still receive exactly the same service from exactly the same address.
Of course, if client 2 reconnected to Router 3, it would have the lowest cost path to server C as long as Server C stayed up. If Server C fails, router 3 would change its route to 3.1.1.1 to the path to Server B.
Operational examples
Anycast works well for any application that is read-only and where the relevant servers have a common database. One common application is the root servers for the Domain Name Service.[3] Another application is in Internet Protocol infrastructure security. Large operators may have multiple sinkholes [4] for analyzing hostile traffic; the sinkhole nearest the ingress router does the analysis of a single-stream denial of service (DoS) attack, while anycast-addressed sinkholes respond well under distributed denial of service (DDoS) attack.
Router interface addresses that are unicast need more care in configuration, but are still feasible.[5] When using anycast with routers, it is best to use a routing protocol, such as the Border Gateway Protocol or Open Shortest Path First, that has an explicit router identifier that can disambiguate different announcements of the same address.
References
- ↑ 1.0 1.1 Hinden, R. & S. Deering. (February 2006), IP Version 6 Addressing Architecture., RFC4291
- ↑ Miller, Kevin (NANOG 29 – October 2003), Deploying IP Anycast
- ↑ Root Server Anycast Status
- ↑ Greene, Barry Raveendran & Danny Macpherson, Sinkholes: A Swiss Army Knife ISP Security Tool Version 1.8
- ↑ John Kristoff (January 2, 2004), Anycast Routing, Anycast Addressing on the Internet